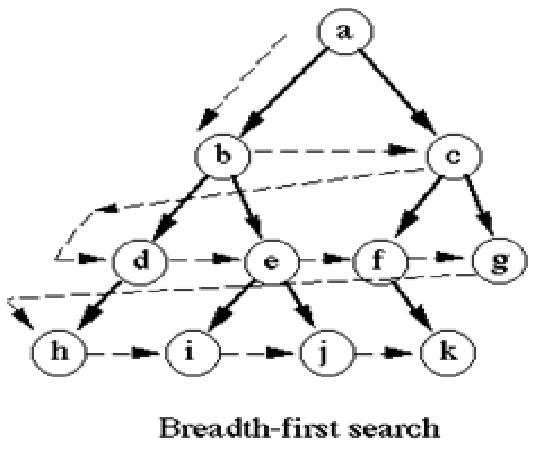
Breadth-first search
Breadth-first search (BFS) is an algorithm for traversing or searching tree or graph data structures. It starts at the tree root (or some subjective node of a graph, sometimes referred to …
Faculty: IT 2019 Sample Papers with Solutions Sr. No. Paper Name Question Paper Link Solution Link 1. Cloud Computing Click Here Click Here 2. Analysis & Design of Algorithm Click Here …
Faculty: IT 2019 Sample Papers with Solutions Sr. No. Paper Name Question Paper Link Solution Link 1. Java Technologies Click Here Click Here 2. Web Technologies Click Here Click Here 3. …
Faculty: IT 2019 Sample Papers with Solutions Sr. No. Paper Name Question Paper Link Solution Link 1. Discrete Mathematics Click Here Click Here 2. Programming in C & C++ Click Here …
Faculty: Science 2019 Sample Papers with Solutions Sr. No. Paper Name Question Paper Link Solution Link 1 Immunology, Virology and Pathogenesis Click Here Click Here 2. Cell Biology Click Here Click …
Faculty: Science 2019 Sample Papers with Solutions Sr. No. Paper Name Question Paper Link Solution Link 1 Plant Biotechnology Click Here Click Here 2. Genetic Engineering Click Here Click Here

Breadth-first search (BFS) is an algorithm for traversing or searching tree or graph data structures. It starts at the tree root (or some subjective node of a graph, sometimes referred to …
Breadth-first search (BFS) is an algorithm for traversing or searching tree or graph data structures. It starts at the tree root (or some subjective node of a graph, sometimes referred to as a ‘search key’) and explores the neighbor nodes first, before moving to the next level neighbors.
BFS was invented in the late 1950s by E. F. Moore, who used it to find the shortest path out of a maze, and discovered independently by C. Y. Lee as a wire routing algorithm.
So traversal is: a, b, c, d, e, f, g, h, i , j, k.
Pseudocode:
Input: A graph Graph and a starting vertex root of G
Output: All vertices reachable from root labeled as explored.
A non-recursive implementation of breadth-first search:
1 Breadth-First-Search (Graph, root):
2
3 for each node n in Graph:
4 n.distance = INFINITY
5 n.parent = NIL
6
7 create empty queue Q
8
9 root.distance = 0
10 Q.enqueue(root)
11
12 while Q is not empty:
13
14 current = Q.dequeue()
15
16 for each node n that is adjacent to current:
17 if n.distance == INFINITY:
18 n.distance = current.distance + 1
19 n.parent = current
20 Q.enqueue(n)
Applications:
Breadth-first search can be used to solve many problems in graph theory, for example:
• Shortest Path and Minimum Spanning Tree for unweighted graph.
• Peer to Peer Networks.
• Social Networking Websites.
• In Garbage Collection.
• Path Finding.
• Finding all nodes within one connected component.
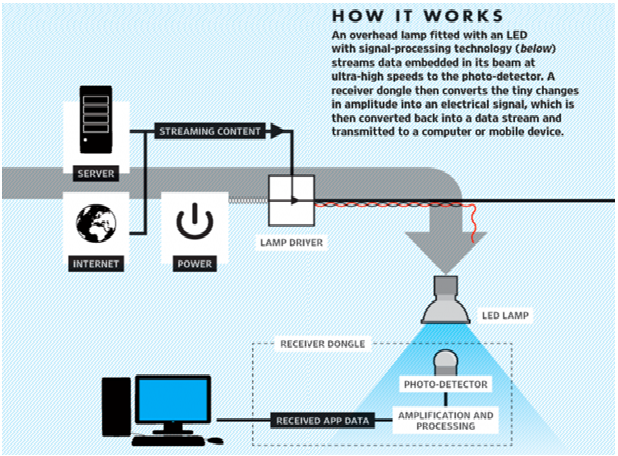
Li-Fi refers to visible light communications (VLC) technology, which delivers high-speed, bidirectional, networked mobile communications in a manner similar to Wi-Fi. It promises huge speed advantages, as well as more-secure communications …
Li-Fi refers to visible light communications (VLC) technology, which delivers high-speed, bidirectional, networked mobile communications in a manner similar to Wi-Fi. It promises huge speed advantages, as well as more-secure communications and reduced device interference.
The term was coined by German physicist Harald Haas during a TED Talk when he outlined the idea of using lightbulbs as wireless routers. That address was delivered four years ago, and many people speculated that, like a lot of apparent revolutionary breakthroughs, Li-Fi would go the way of other “next big things” and not come to fruition. A year after his TED Talk, though, Haas, a professor of mobile communications at the University of Edinburgh, created pureLiFi with a group of people who had been researching the technology since 2008. The company has claimed to be the “recognized leaders in Li-Fi technology” and has already produced two products.
Working of LIFI
When a constant current is applied to an LED [light-emitting-diode] lightbulb, a constant stream of photons is emitted from the bulb which is observed as visible light. If the current is varied slowly, the output intensity of the light dims up and down. Because LED bulbs are semiconductor devices, the current, and hence the optical output, can be modulated at extremely high speeds which can be detected by a photodetector device and converted back to electrical current. The intensity modulation is imperceptible to the human eye, and thus communication is just as seamless as RF [radio frequency technology]. Using this technique, high-speed information can be transmitted from an LED lightbulb.
Disadvantages:
Because Li-Fi technology uses visible light as its means of communication, it won’t work through walls. This means that to have a Li-Fi network throughout your house, you will need these lightbulbs in every room (and maybe even the fridge) to have seamless connectivity.
Another major issue is that Li-Fi does not work outdoors, meaning that public Li-Fi will not be able to replace public Wi-Fi networks any time soon. While Li-Fi’s employment in direct sunlight won’t be possible, pureLiFi said that through the use of filters the technology can be used indoors even when sunlight is present.
Of course, one of the biggest drawbacks is the fact the light needs to be on all the time to deliver connectivity. While that’s not going to be an issue in industrial and retail environments, it’s will be both environmentally and practically problematic in domestic settings.
When Will Li-Fi Light bulbs Be Available?
Speaking to International Business Times UK this week, Deepak Solanki, CEO of Velmenni, said the technology could reach consumers in three to four years. “We are doing a few pilot projects within different industries where we can utilize the VLC technology,” Solanki said. “Currently, we have designed a smart-lighting solution for an industrial environment where the data communication is done through light. We are also doing a pilot project with a private client where we are setting up a Li-Fi network to access the Internet in their office space.”

WHAT IS BLUE EYES TECHNOLOGY? Aims at creating computational machines that have perceptual and sensory ability. Use camera and microphone to identify user actions and emotions The term BLUE …
WHAT IS BLUE EYES TECHNOLOGY?
Aims at creating computational machines that have perceptual and sensory ability.
Use camera and microphone to identify user actions and emotions
The term BLUE EYES:-
BLUE in the term stands for Bluetooth, which enables reliable wireless communication
EYES, because the eye movement enables us to obtain a lot of interesting and important information.
NEED OF BLUE EYES TECHNOLOGY:-
To built a machine that can understand your emotions
A pc that can listen, talk or scream
Verify your identity, feels your presence and interact with you.
TECHNOLGIES USED:-
Emotion Mouse
Manual And Gaze Input Cascaded (MAGIC)
Artificial Intelligent Speech Recognition
The eye movement Sensor
EMOTION MOUSE:-
Simplest way
People spend approximately 1/3 of their total computer time touching input device
Physiological data is obtained and emotional state is determined
MAGIC POINTING:-
Reduce the cursor movement needed for target selection
Click on the target with a regular manual input device
Two magic pointing techniques
Liberal
Conservative
APPROACHES:-
LIBERAL APPROACH:- To warp the cursor to every new object user looks.
CONSERVATIVE APPROACH:- Does not warp the cursor target until the manual input device has been actuated.
SPEECH RECOGNITION:-
Input words are scanned and matched against internally stored words
Identification causes some action to be taken User speaks to the computer through microphone
Filtered and fed to ADC and then stored in RAM
THE EYE MOVEMENT SENSOR DESIGNING:-
A personal area network for linking all the operators and the supervising system
Two major units
– DAU (data acquisition unit )
– CSU (central system unit )
DAU:-
The DAU consists of the following components
ATMEL 8952 microcontroller
BLUE TOOTH MODULE – supports synchronous voice
data transmission
central system sound feedback
ALPHAUNUMERIC LCD display
LED indicators
DAU – features:-
Lightweight
Runs on batteries – low power consumption
Easy to use – does not disturb the operator working
ID cards for operator authorization
Voice transmission using hardware PCM codec
CSU – components:-
CONNECTION MANAGER – main task to perform low-level blue tooth communication
DATA ANALYSIS MODULE – performs the analysis of the raw sensor data
DATA LOGGER MODULE – provides support for storing the monitored data.
VISULAIZATION MODULE – provides user interface for the supervisors
Data security:-
Only registered mobile devices can connect to the system
Bluetooth connection authentication
Bluetooth connection encryption
Access rights restrictions Personal and physiological data encryption
Applications:-
In retailing record and interpret customer movements
In automobile industry
In video games
To create “Face Responsive Display” and “Perceptive Environment” Generic control rooms
Ellipse is an elongated form of circle or in other words, circle is an special case of ellipse where the two radii of the circle are equal. Cvc An ellipse explained …
Ellipse is an elongated form of circle or in other words, circle is an special case of ellipse where the two radii of the circle are equal. Cvc An ellipse explained as a set of points such that the sum of distances from two fixed points (foci) is same for all points given a point P = (x, y), distances are d1 & d2, equation is :
d1 + d2 = constant _ _ _ (1)
In terms of local coordinates
F1 = (x1, y1) & F2 (x2, y2)
Equation is :
_ _ _ (2)
This can also be written in the form :
Ax2 + By2 + Cxy + Dx + Ey + F = 0 _ _ _ (3)
(More A, B, C, D, E, & F are evaluated in terms of focal coordinates & major minor axis).
• Major axis – which extends form 1 point to other through foci.
• Minor axis – which spans the shouter dimension bisecting major axis at ellipse center.
An interactive method for specifying an ellipse in an arbitrary orientation is to input two foci & a point on ellipse boundary & evaluate constant in equation (1) & so on.
Equation can be simplified if ellipse is in “standard position” with major & minor axis oriented parallel to x and y axis.
y
yc
xc x
= 1 _ _ _(4)
Now using polar coordinates r & θ
Parameter equations are :
x = xc + rx cos θ
y = yc + ry sin θ

TalkTalk, a British phone and broadband provider with more than four million customers, disclosed Friday that intruders had hacked its Web site and may have stolen personal and financial data. Sources …
TalkTalk, a British phone and broadband provider with more than four million customers, disclosed Friday that intruders had hacked its Web site and may have stolen personal and financial data. Sources close to the investigation say the company has received a ransom demand of approximately £80,000 (~USD $122,000), with the attackers threatening to publish the TalkTalk’s customer data unless they are paid the amount in Bitcoin.
In a statement on its Web site, TalkTalk said a criminal investigation was launched by the Metropolitan Police Cyber Crime Unit following “a significant and sustained cyberattack on our website.”
“That investigation is ongoing, but unfortunately there is a chance that some of the following data has been compromised: names, addresses, date of birth, phone numbers, email addresses, TalkTalk account information, credit card details and/or bank details,” the statement continues. “We are continuing to work with leading cyber crime specialists and the Metropolitan Police to establish exactly what happened and the extent of any information accessed.”
A source close to the investigation who spoke on condition of anonymity told KrebsOnSecurity that the hacker group who demanded the £80,000 ransom provided TalkTalk with copies of the tables from its user database as evidence of the breach. The database in question, the source said, appears related to at least 400,000 people who have recently undergone credit checks for new service with the company. However, TalkTalk’s statement says it’s too early to say exactly how many customers were impacted. “Identifying the extent of information accessed is part of the investigation that’s underway,” the company said.
Separately, promises to post the stolen data have appeared on AlphaBay, a Deep Web black market that specialized in selling stolen goods and illicit drugs. The posting was made by someone using the nickname “Courvoisier.” This member, whose signature describes him as “Level 6 Fraud and Drugs seller,” appears to be an active participant in the AlphaBay market with many vouches from happy customers who’ve turned to him for illegal drugs and stolen credit cards, among other goods and services.
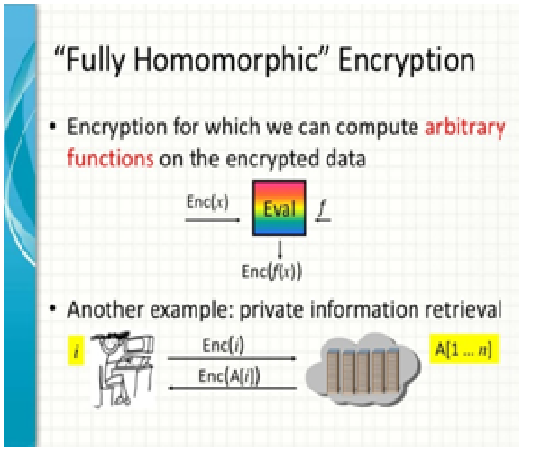
Homomorphism Encryption (HE) provides a solution to the problem of outsourcing computations privately to a cloud. There are a number of Somewhat Homomorphism Encryption (SHE) schemes that support many additions but …
Homomorphism Encryption (HE) provides a solution to the problem of outsourcing computations privately to a cloud. There are a number of Somewhat Homomorphism Encryption (SHE) schemes that support many additions but only a limited number of multiplications. Though SHE schemes can evaluate only a limited set of circuits compared to FHE schemes, it is at rest motivating to believe them for application chiefly for competence motive. Those SHE schemes that support only a single operation on cipher texts – addition or multiplication – is called linearly homomorphism. That is, (additive) linearly-homomorphism encryption scheme can estimate barely linear function on top of cipher texts.
The major problem address in the present job is to allow assessment of degree-two function using linearly-homomorphism encryption scheme. To this end, the author offer a general conversion that extend an (additively-written) linearly-homomorphism format to carry a solitary development procedure so that it will now be able to evaluate a subset of functions of degree two. The only requirement of the underlying linearly-homomorphism scheme is that it should be public space, which means that the communication room must be a openly known limited commutative circle and that it is probable to efficiently sample a random element from this ring. This property seem to hold for nearly the entire recognized linearly-homomorphism encryption scheme or can be simply modified to become so.
Density is single of the three main materials of a (fully) HE system that say so as to the difficulty of decryption must exist autonomous of the complexity of the route evaluate the given function. The other two requirements are semantic safety and route solitude for the underlying plaintext mail. The latter means that it must not be possible to learn anything regarding the post in the code texts input to a occupation It is exposed that the proposed transformation conserve semantic safety and the distorted format will be leveled circuit private if the underlying scheme is circuit classified. The distorted system will be clever to compactly evaluate a subset of degree-two functions (represented as polynomials) [Math Processing Error] consisting of the following polynomials [Math Processing Error]
where [Math Processing Error], [Math Processing Error], [Math Processing Error] are linear polynomials. It turns out that the subclass [Math Processing Error] of quadratic polynomials is applicable, for example, SPDZ protocol for multi-party computation requires a HE scheme for [Math Processing Error] with [Math Processing. A transformation of the underlying HE scheme is given in this model that is similar to the previous alteration, using which it is now possible to evaluate any quadratic polynomial compactly. Interestingly, the former (single-server) change preserves other property such as zero-knowledge proof of plaintext information, threshold decryption, and multi-key homomorphicity.
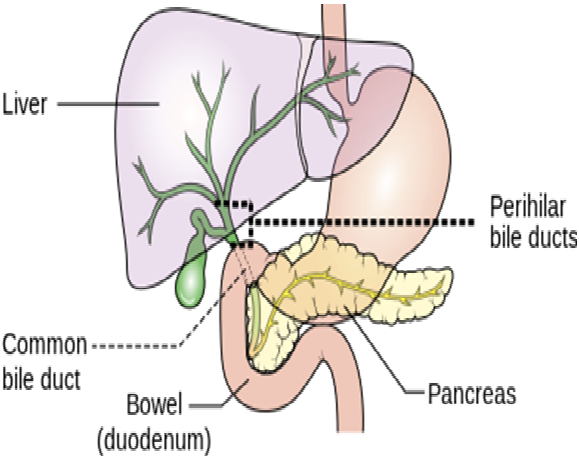
Definition The liver is a gland and plays a major role in metabolism with numerous functions in the human body, including regulation of glycogen storage, decomposition of red blood cells, plasma …
Definition
The liver is a gland and plays a major role in metabolism with numerous functions in the human body, including regulation of glycogen storage, decomposition of red blood cells, plasma protein synthesis, hormone production, and
Structure
The liver is a reddish brown wedge-shaped organ with four lobes of unequal size and shape. A human liver normally weighs 1.44–1.66 kg. It is both the largest internal organ and the largest gland in the human body. Located in the right upper quadrant of the abdominal cavity, it rests just below the diaphragm, to the right of the stomach and overlies the gallbladder.
The liver is connected to two large blood vessels: the hepatic artery and the vein. The hepatic artery carries oxygen-rich blood from the aorta, whereas the portal vein carries blood rich in digested nutrients from the entire gastrointestinal tract and also from the spleen and pancreas. These blood vessels subdivide into small capillaries known as liver sinusoids, which then lead to a lobule.
Lobules are the functional units of the liver. Each lobule is made up of millions of hepatic cells (hepatocytes) which are the basic metabolic cells. The lobules are held together by fine areolar tissue which extends into the structure of the liver, by accompanying the vessels (veins and arteries) ducts and nerves through the hepatic portal, as a fibrous capsule called Glisson’s capsule. The whole surface of the liver is covered in a serous coat derived from peritoneum and this has an inner fibrous coat (Glisson’s capsule) to which it is firmly adhered.
Function
• Production of bile, which helps carry away waste and break down fats in the small intestine during digestion
• Production of certain proteins for blood plasma
• Production of cholesterol and special proteins to help carry fats through the body
• Store and release glucose as needed
• Processing of hemoglobin for use of its iron content (the liver stores iron)
• Conversion of harmful ammonia to urea (urea is one of the end products of protein metabolism that is excreted in the urine)
• Clearing the blood of drugs and other harmful substances
• Regulating blood clotting
• Resisting infections by producing immune factors and removing bacteria from the bloodstream
• Clearance of bilirubin (if there is a buildup of bilirubin, the skin and eyes turn yellow)
Blood Supply
The liver receives a dual blood supply from the hepatic portal vein and hepatic arteries. The hepatic portal vein delivers approximately 75% of the liver’s blood supply, and carries venous blood drained from the spleen, gastrointestinal tract, and its associated organs. The hepatic arteries supply arterial blood to the liver, accounting for the remaining quarter of its blood flow. Oxygen is provided from both sources; approximately half of the liver’s oxygen demand is met by the hepatic portal vein, and half is met by the hepatic arteries.
Blood flows through the liver sinusoids and empties into the central vein of each lobule. The central veins coalesce into hepatic veins, which leave the liver and drain into the inferior vena cava.
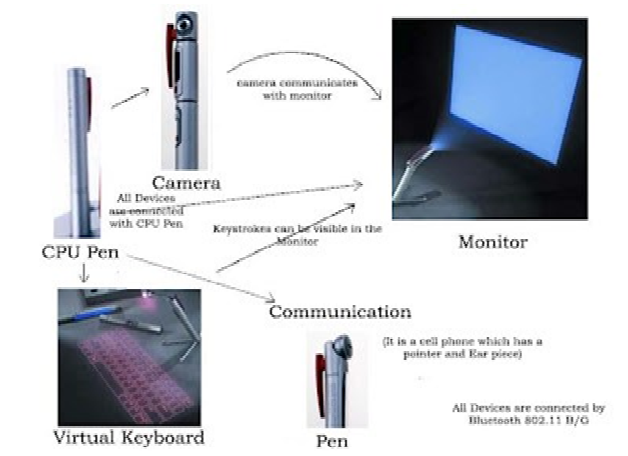
Today’s era is considered to be as new world era. In the modern world, communication technology is rapidly growing. And of course the computer is the main communication machine used. Since …
Today’s era is considered to be as new world era. In the modern world, communication technology is rapidly growing. And of course the computer is the main communication machine used. Since the time computer has been make-believe scientists and engineers have been trying making it more and more compact. Some of the results we have found in the form of Mobiles I-pods and I-phones have replaced the laptops or desktops to an extent. But the scientist is now making an effort on making it more compact even than mobile. There are computers in the shape of different pens each having a function of its own and when combined together give us the usage of a full-blown computer. It is a computer broken down apart into pieces, each the size of a pen. The screen and keyboard are projected onto surfaces.
Components: Following are the components of 5 pen technology-
Virtual Keyboard:
The Virtual Laser Keyboard (VKB) is the new widget for PC users. The VKB emits laser on to the desk where it looks like the keyboard having QWERTY arrangement of keys i.e., it uses a laser beam to generate a full-size perfectly operating laser keyboard that easily connects to of PC and Most of the handheld devices including PDA’s or tablet PC’s.
Battery:
It is an vital component in the moveable type of computer. Ideal batteries must be small in size and work for longer time. It comes with a battery life of 6+. If we talk about its usage, it can be used for 2 weeks.
Advantage of this 5 pen PC technology:
• It is Portable i.e can be carried
• It is Feasible
• Ultimate ever-present
• Support WiFi technology
• Pens produce both the monitor as well as the keyboard on any flat surfaces from where you can carry out functions.
Disadvantages:
• Positioning is more important to use it to up to the optimum level.
• Keyboard concept is not new.
• It is currently unclear
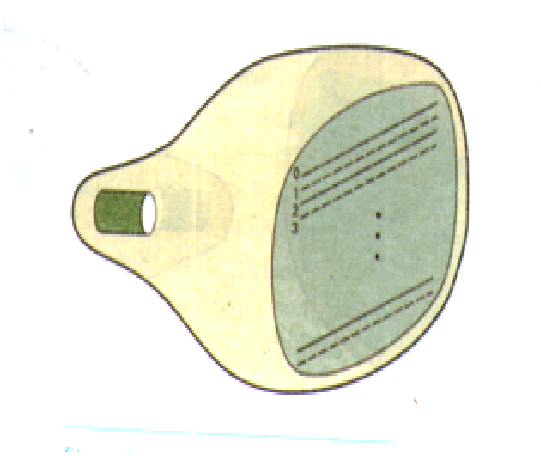
The arrangement of a simple random scan system is shown in the following figure. System stores and application program in the system memory along with a graphics package. With the help …
The arrangement of a simple random scan system is shown in the following figure. System stores and application program in the system memory along with a graphics package. With the help of graphics package the Graphics command in the application program are converted into a display file stored in the system memory. And this file helps the system to refresh the screen. When operated as a random-scan display unit, a CRT has the electron beam directed only to the parts of the screen where a picture is to be drawn. Random-scan monitor draw a picture one line at a time and for this reason are also referred to as vector displays (or stroke-writing of calligraphic displays).
The component lines of a picture can be drawn and refreshed by a random-scan system in any specified order Fig. a pen plotter in a similar way and is an example of a random-scan, hard-copy device.
Refresh rate on a random-scan system depends on the number of lines to be displayed. Picture definition is now stored as a set of line-drawing commands in an area of memory referred to as the refresh display file. Sometimes the refresh display file is called the display list, display program,
C++ began as an expanded version of C. The C++ extensions were first invented by Bjarne Stroustrup in 1979 at Bell Laboratories in Murray Hill, New Jersey. He initially called the …
C++ began as an expanded version of C. The C++ extensions were first invented by Bjarne Stroustrup in 1979 at Bell Laboratories in Murray Hill, New Jersey. He initially called the new language “C with Classes.” However, in 1983 the name was changed to C++.Although C was one of the most liked and widely used professional programming languages in the world, the invention of C++ was necessitated by one major programmingfactor: increasing complexity. Over the years, computer programs have become
larger and more complex.
Even though C is an excellent programming language, it has its limits. In C, once a program exceeds from 25,000 to 100,000 lines of code, it becomes so complex that it is difficult to grasp as a totality. The purpose of C++ is to allow this barrier to be broken. The essence of C++ is to allow the programmer to comprehend and manage larger, more complex programs
Object-Oriented Programming:
Since object-oriented programming (OOP) drove the creation of C++, it is necessary to understand its foundational principles. OOP is a powerful way to approach the job of programming. Programming methodologies have changed dramatically since the invention of the computer, primarily to accommodate the increasing complexity of programs.
For example, when computers were first invented, programming was done by toggling in the binary machine instructions using the computer’s front panel. As long as programs were just a few hundred instructions long, this approach worked. As programs grew, assembly language was invented so that a programmer could deal with larger, increasingly complex programs, using symbolic representations of the machine instructions. As programs continued to grow, high-level languages were introduced that gave the programmer more tools with which to handle complexity.
The first widespread language was, of course, FORTRAN. Although FORTRAN was a very impressive first step, it is hardly a language that encourages clear, easy-to understand programs.
The 1960s gave birth to structured programming. This is the method encouraged by languages such asCand Pascal. The use of structured languages made it possible to write moderately complex programs fairly easily. Structured languages are characterized by their support for stand-alone subroutines, local variables, rich control constructs, and their lack of reliance upon the GOTO. Although structured languages are a powerful tool, even they reach their limit when a project becomes too large.
Object-oriented programming took the best ideas of structured programming and combined them with several new concepts. The result was a different way of organizing a program. In the most general sense, a program can be organized in one of two ways: around its code (what is happening) or around its data (who is being affected). Using only structured programming techniques, programs are typically organized around code. This approach can be thought of as “code acting on data.”
For example, a program written in a structured language such as C is defined by its functions, any of which may operate on any type of data used by the program. Object-oriented programs work the other way around. They are organized around data, with the key principle being “data controlling access to code.” In an object-oriented language, you define the data and the routines that are permitted to act on that data. Thus, a data type defines precisely what sort of operations can be functional to that data.
Encapsulation:
Encapsulation is the mechanism that binds together code and the data it manipulates, and keeps both safe from outside interference and misuse. In an object-oriented language, code and data may be combined in such a way that a self-contained “black box” is created. When code and data are linked together in this fashion, an object is created.
In other words, an object is the device that supports encapsulation. Within an object, code, data, or both may be private to that object or public. Private code or data is known to and accessible only by another part of the object. That is, private code or data may not be accessed by a piece of the program that exists outside the object. When code or data is public, other parts of your program may access it even though it is defined within an object. Typically, the public parts of an object are used to provide a controlled interface to the private elements of the object.
For all intents and purposes, an object is a variable of a user-defined type
Polymorphism:
Object-oriented programming languages support polymorphism, which is characterized by the phrase “one interface, multiple methods.” In simple terms, polymorphism is the attribute that allows one interface to control access to a general class of actions. The specific action selected is determined by the exact nature of the situation. A real-world example of polymorphism is a thermostat. No matter what type of furnace your house has (gas, oil, electric, etc.) , the thermostat works the same way. In this case, the
Thermostat (which is the interface) is the same no matter what type of furnace (method) you have. For example, if you want a 70-degree temperature, you set the thermostat to 70 degrees. It doesn’t matter what type of furnace actually provides the heat. This same principle can also apply to programming.
Inheritance
Inheritance is the process by which one object can acquire the properties of another object. This is important because it supports the concept of classification. If you think about it, most knowledge is made manageable by hierarchical classifications. For example, a Red Delicious apple is part of the classification apple, which in turn is part of the fruit class, which is under the larger class food.

