Mobile IP
Mobile IP is an Internet Engineering Task Force (IETF) standard communications protocol. In many applications (e.g., VPN, VoIP) sudden changes in network connectivity and IP address can cause problems. Mobile IP …
Mobile IP is an Internet Engineering Task Force (IETF) standard communications protocol. In many applications (e.g., VPN, VoIP) sudden changes in network connectivity and IP address can cause problems. Mobile IP protocols were designed to support seamless and continuous internet connectivity. Mobile IP was developed as a means for transparently dealing with problems of mobile users. It enables hosts to stay connected to the Internet regardless of their location and to be tracked without needing to change their IP address. It requires no modifications to IP addresses or IP address format. It has no geographical limitations.
Mobile IP Entities
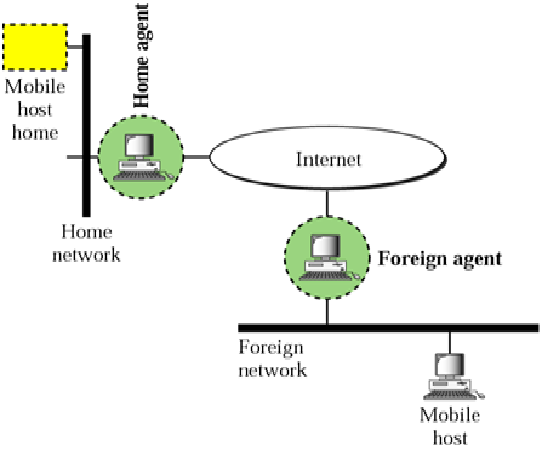
• Mobile Node (MN)It is the entity that may change its point of attachment from network to network in the Internet. MN assigned a permanent IP called its home address to which other hosts send packets regardless of MN’s location. Since this IP doesn’t change it can be used by long-lived applications as MN’s location changes.
• Home Agent (HA): This is a router with additional functionality. It is Located on home network of MN. HA does mobility binding of MN’s IP with its COA (care of address). It forwards packets to appropriate network when MN is away.
• Foreign Agent (FA): it is a router with enhanced functionality. If MN is away from HA, it uses an FA to send/receive data to/from HA. FA advertises itself periodically. It forwards MN’s registration request. FA de-encapsulates messages for delivery to MN.
• Care-of-address (COA): It is an address which identifies MN’s current location. This address is sent by FA to HA when MN attaches. It is usually the IP address of the FA.
• Correspondent Node (CN): CN is the end host to which MN is corresponding (e.g. a web server).
Home agent and foreign agent
Mobile IP Operations
o A MN listens for agent advertisement and then initiates registration. If responding agent is the HA, then mobile IP is not necessary.
o After receiving the registration request from a MN, the HA acknowledges and registration is complete. Registration happens as often as MN changes networks.
o HA intercepts all packets destined for MN. This is simple unless sending application is on or near the same network as the MN. HA masquerades as MN. There is also a de-registration process with HA if an MN returns home.
o HA then encapsulates all packets addressed to MN and forwards them to FA
o FA de-encapsulates all packets addressed to MN and forwards them via hardware address (learned as part of registration process)
Enhancements to the Mobile IP standard, such as Mobile IPv6 and Hierarchical Mobile IPv6 (HMIPv6), were developed to advance mobile communications by making the processes involved less cumbersome.