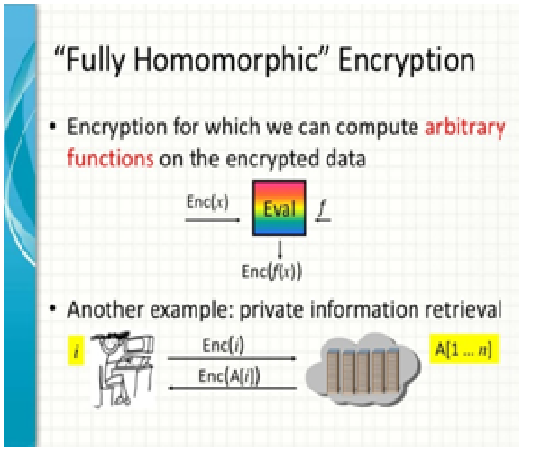
Homomorphism Encryption (HE) provides a solution to the problem of outsourcing computations privately to a cloud. There are a number of Somewhat Homomorphism Encryption (SHE) schemes that support many additions but only a limited number of multiplications. Though SHE schemes can evaluate only a limited set of circuits compared to FHE schemes, it is at rest motivating to believe them for application chiefly for competence motive. Those SHE schemes that support only a single operation on cipher texts – addition or multiplication – is called linearly homomorphism. That is, (additive) linearly-homomorphism encryption scheme can estimate barely linear function on top of cipher texts.
The major problem address in the present job is to allow assessment of degree-two function using linearly-homomorphism encryption scheme. To this end, the author offer a general conversion that extend an (additively-written) linearly-homomorphism format to carry a solitary development procedure so that it will now be able to evaluate a subset of functions of degree two. The only requirement of the underlying linearly-homomorphism scheme is that it should be public space, which means that the communication room must be a openly known limited commutative circle and that it is probable to efficiently sample a random element from this ring. This property seem to hold for nearly the entire recognized linearly-homomorphism encryption scheme or can be simply modified to become so.
Density is single of the three main materials of a (fully) HE system that say so as to the difficulty of decryption must exist autonomous of the complexity of the route evaluate the given function. The other two requirements are semantic safety and route solitude for the underlying plaintext mail. The latter means that it must not be possible to learn anything regarding the post in the code texts input to a occupation It is exposed that the proposed transformation conserve semantic safety and the distorted format will be leveled circuit private if the underlying scheme is circuit classified. The distorted system will be clever to compactly evaluate a subset of degree-two functions (represented as polynomials) [Math Processing Error] consisting of the following polynomials [Math Processing Error]
where [Math Processing Error], [Math Processing Error], [Math Processing Error] are linear polynomials. It turns out that the subclass [Math Processing Error] of quadratic polynomials is applicable, for example, SPDZ protocol for multi-party computation requires a HE scheme for [Math Processing Error] with [Math Processing. A transformation of the underlying HE scheme is given in this model that is similar to the previous alteration, using which it is now possible to evaluate any quadratic polynomial compactly. Interestingly, the former (single-server) change preserves other property such as zero-knowledge proof of plaintext information, threshold decryption, and multi-key homomorphicity.